
3 – Programming to treat votes as decimals –
The term “DOUBLE” means to store and process numbers with “double precision floating points” – in other words, to enable large numbers of decimal values.
In contrast, the term “INT” instructs the program to treat numbers as whole integers.
Source Code:
Below are clips from GEMS source code showing that it converts votes from whole numbers (previous version, GEMS 1.17) to store and process them as decimal values by setting them to “double” in GEMS version 1.18:
“ALTER TABLE SumCandidateCounter”
“ALTER COLUMN TotalVotes DOUBLE”
“ALTER TABLE SumRaceCounter”
“ALTER COLUMN NumberOfUnderVotes DOUBLE”
***
“CREATE TABLE SumCandidateCounter (
ReportunitId INT,
VCenterId INT,
CounterGroupId INT,
CandVGroupId INT,
TotalVotes DOUBLE )”
***
“CREATE TABLE SumRaceCounter (
ReportunitId INT,
VCenterId INT,
CounterGroupId INT,
RaceId INT,
TimesCounted INT,
TimesBlankVoted INT,
TimesOverVoted INT,
NumberOfUnderVotes DOUBLE ) ”
***
“ALTER TABLE CandidateCounter ”
“ALTER COLUMN TotalVotes DOUBLE ”
“ALTER TABLE RaceCounter ”
“ALTER COLUMN NumberOfUnderVotes DOUBLE”
***
# Contains the candidate counts for the race
“CREATE TABLE CandidateCounter (
CounterBatchId INT,
ReportunitId INT,
CounterGroupId INT,
CandVGroupId INT,
TotalVotes DOUBLE
# Number of votes ) ”
***
“CREATE TABLE SumCandidateCounter (
ReportunitId INT,
VCenterId INT,
CounterGroupId INT,
CandVGroupId INT,
TotalVotes DOUBLE ) “
***
Non-programmers may not have seen the term "double" used to describe processing numbers with decimals.
Here is an SQL tutorial -- there are many -- showing that "Double" means to process numbers as decimal values:

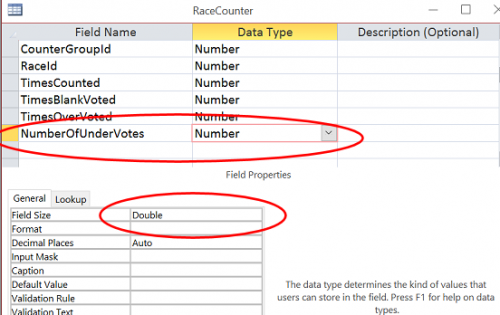
The above source code instructions create and define data structures in Microsoft Access tables, used by GEMS to create results reports. By opening the GEMS tables using MS Access, and right-clicking “design view” for the tables related to vote-counting, you see that the instruction to treat vote counts as “double” is implemented. The vote format in each is set to “double,” counting votes as decimals.
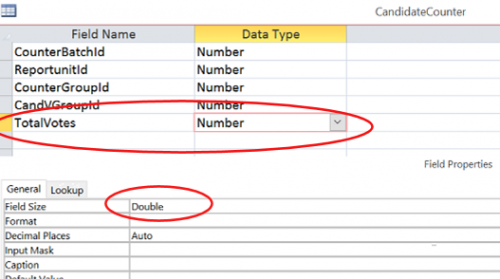

Overvotes are counted as whole numbers but undervotes are counted as decimals:

Because the “double” configuration for votes is built into the source code, the most important requirement for sophisticated, configurable election tampering exists wherever the program is used.
Next:
Part 4: Presidential race in an entire state switched in four seconds http://blackboxvoting.org/fraction-magic-4
Previous:
Part 2: Context, Background, Deeper, Worse http://blackboxvoting.org/fraction-magic-2
All:
Part 1: Votes are being counted as fractions instead of as whole numbers http://blackboxvoting.org/fraction-magic-1
Part 2: Context, Background, Deeper, Worse http://blackboxvoting.org/fraction-magic-2
Part 3: Proof of code http://blackboxvoting.org/fraction-magic-3
Part 4: Presidential race in an entire state switched in four seconds http://blackboxvoting.org/fraction-magic-4
Part 5: Masters of the Universe http://blackboxvoting.org/fraction-magic-5
Part 6: Execution capacity – coming – http://blackboxvoting.org/fraction-magic-6
Part 7: Solutions and Mitigations – coming – http://blackboxvoting.org/fraction-magic-7
* * * * *
 Bev Harris is a writer and founder of Black Box Voting. She has researched and written about election transparency and computerized voting systems since 2002. Harris was featured in the Emmy-nominated HBO documentary Hacking Democracy, and is the author of Black Box Voting: Ballot Tampering in the 21st Century, a book purchased by the White House Library and also reportedly found on Osama bin Laden’s bookshelf. Harris’s research has been covered in The New York Times, Vanity Fair, Time Magazine, CNN and several international publications, including the Philippine Daily Inquirer and Agence France Presse. Contact by text or phone 206-335-7747 for media inquiries.
Bev Harris is a writer and founder of Black Box Voting. She has researched and written about election transparency and computerized voting systems since 2002. Harris was featured in the Emmy-nominated HBO documentary Hacking Democracy, and is the author of Black Box Voting: Ballot Tampering in the 21st Century, a book purchased by the White House Library and also reportedly found on Osama bin Laden’s bookshelf. Harris’s research has been covered in The New York Times, Vanity Fair, Time Magazine, CNN and several international publications, including the Philippine Daily Inquirer and Agence France Presse. Contact by text or phone 206-335-7747 for media inquiries.
 Bennie Smith is a Memphis-based application developer for an electrical manufacturing company. He is also a political strategist who has developed a micro-targeting application that predicts voter turnout. In August 2014 he was approached by a number of candidates who insisted that their elections had been stolen. He disagreed with the group and offered to look into how the system works. After discovering a number of irregularities, Smith began to research how votes that originate from the same source can change once they get into the GEMS vote tabulation program. Smith’s attention to these anomalies uncovered an extraordinarily high-risk tampering mechanism and ultimately provided a new infrastructure for analyzing questionable election results.
Bennie Smith is a Memphis-based application developer for an electrical manufacturing company. He is also a political strategist who has developed a micro-targeting application that predicts voter turnout. In August 2014 he was approached by a number of candidates who insisted that their elections had been stolen. He disagreed with the group and offered to look into how the system works. After discovering a number of irregularities, Smith began to research how votes that originate from the same source can change once they get into the GEMS vote tabulation program. Smith’s attention to these anomalies uncovered an extraordinarily high-risk tampering mechanism and ultimately provided a new infrastructure for analyzing questionable election results.
* * * * *
